Random carousel of articles
WordPress: Transform Your Experience with Subdirectories
My site is blocked! Unlock URL access with content filtering companies
“Hello can you hear me”: Social engineering or part of the call?
Computer security hardening – safeguarding your systems
Putting your computer in chains is one way of hardening the system Computer Security. Kind…
Brighten Your Website: How to Remove the Default Featured Image Shading in WordPress 2019 Theme
Exploiting the SDLC: Unleashing the Devastating Power of Cyber Warfare
The Ups and Downs: Exploring the Journey of InMotion Hosting – A Revealing Two-Year Review
Reviving Your Website: Dead Link Checkers for Seamless Online Experiences
The end of the (land) line
So you’ve looked at your local phone bill and it was… oh my, I’m paying…
HostMantis WordPress web hosting review – Excellent A1!
Unveiling the Top Free Internet Faxing Providers
Data Breaches Unmasked: The Devastating Reality of Identity Theft
Watering Hole attack: Cybercriminals subvert your most vulnerable favorite websites
Bulletproof Your Website: Enhancing WordPress Security with File System Protection for Login
Vishing Scams: How to Safeguard Yourself from Deceptive Voice Attacks
Domain Dilemma: The Pitfalls of Free Domains and the Benefits of Owning Your Own
Safeguarding your domain search: how to avoid ‘front runners’
Computer Security Incident Response (NIST SP800-61r2)
The best free video editors for vlogging, YouTube, and more!
Defending Your Wallet: Unveiling the Thrilling World of Payment Card Theft and How to Stay Safe
WordPress Plugins (1.0 Introduction)
WordPress is an incredible Content Management System — and it is free! WordPress off the…
WordPress Post Revisions
WordPress Plugins – 2.1 Mail Relay
Let me ask an honest question. Would you rather be doing business with “bobrx153@hotmail.com” or…
Zero day, 0day, ohday, oh my!
Hackers have a few things in their favor when it comes to getting into your…
Using Artificial Intelligence to create predictive systems
The term Artificial Intelligence (or AI) was coined in the mid 1950s. AI technology was…
Exploring advantages and disadvantages of Cloud: IAAS PAAS SAAS
Enhancing Security: Protecting Networks with Outbound Firewall Rules
Protecting Your Personal Privacy at Work: Tips for Confidentiality and Security
Python paradise: Ditch the setup, soar with cloud Python
Are you an experienced Python programmer? Then this article is absolutely for you. On the…
Medical Device Cyber Security: Challenges, Guidance, and Best Practices for Secure Deployment
Last update: 2023-08-04 1. Background Cyberattacks on medical devices are a growing threat to patient…
Risk management – developing a framework
Risk management is an essential skill for any business professional. Whether it be having a…
Breaking the glass: Mastering BreakGlass Techniques for Emergency Access
WordPress Plugins – 2.1 Interact with your users – Mailjet Outbound mail relay
Link Tracking: Unveiling the best Tracker websites with enhanced analytics
How to secure FDA approved medical devices from hackers
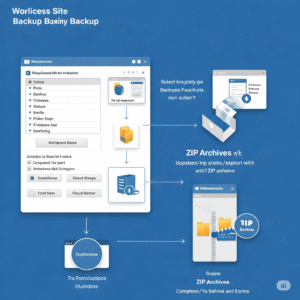
Enable Zip Archive for Duplicator in HostMantis
Are you using a utility that requires Zip Archive Enabled in WordPress? For me, this…
Identity theft
The first rule of security: “Be aware” of your surroundings
Business Continuity Planning
Business Continuity Planning (BCP) is the pre-planning effort put in to make sure your business…
Centrally managing WordPress sites
Managing multiple WordPress sites is no easy task. While managing a single WordPress site in…
Where to find “free use licensed” photos and videos
WordPress Plugins (2.0 Security: Confidentiality, Integrity, Availability)
This post is a part of the WordPress Plugins discussion threads and focuses on Plugins…
HostMantis Review: Seriously Good and Reliable Web Hosting!
Diving into the world of web hosting can feel like navigating a complex network, a…
Phish for phun and profit
Phishing is a real problem, and that problem is only increasing in frequency. Phish attacks…
LinkedIn Mastery: Elevate Your Career with Proven Strategies for Success
Coronavirus special report: Separating your Work and Personal identities
Unmasking The Future Of Malware with ChatGPT: A Comprehensive Analysis And Expert Commentary On The Evolving Threat Landscape
“The future of malware” is a trigger for most of us in computer security. Most…