This post is a part of the WordPress Plugins discussion threads and focuses on Plugins that increase the Security of your WordPress site. Just as with all WordPress Plugin recommendations, only “free” Plugins will be considered.
Security
First, a definition for this very important section. Security is protecting the Confidentiality, Integrity, and Availability of a system. We’ll be examining WordPress Plugins that help to achieve:
- Confidentiality: Protecting information so as it is only available to those who have permission to know. Protecting information against observation from every other user.
- Integrity: Does it relate to hackers defacing a web site? Can it look like one person is posting, when in fact someone else is posting? Can attribution of the information change? Are there controls in place to confirm the identity of the person interacting with the web site?
- Availability: Is the information protected against System outages? Is the data available within an allowable speed constraint?
As a reminder, if you do add any plugins to your site — especially security related plugins — be sure to test the site in either an incognito browser, or a different computer altogether before logging out of the session where you set up the Plugin. Make sure the new Plugin doesn’t break something! I’ve had to log into cPanel more than once to disable a dastardly plugin. It is just no fun.
I considered announcing one of the headlines as “Software Firewall”. Let me let that sink in for a moment. Firewall.
Saying “Firewall!” is like saying “National Security!” — you get everyone’s attention, even if it really doesn’t mean anything. No one may understand what you are asking or what you are saying, but I guarantee you’ll get attention if you say either of these terms.
But the problem with my section was that Firewall is not the problem that we are trying to solve. Firewall may be a solution to a problem, but it isn’t the problem itself. Because this article is written in terms of identifying “security functions” and only then identifying solutions to those problems, I’ll focus on problems first. Here goes.
Protect against random bots
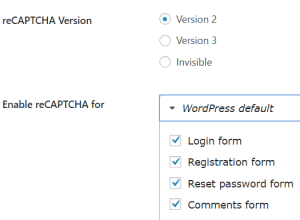
Have you noticed drive by spam? This would include emails through your contact form from bots or from people who you know are not interested in your product. The first day I installed WordPress, I received a dozen spam, likely from bots. How to fix random drive by bots? CAPTCHA is one way to slow them down.
Over time, some toolsets become obsolete or otherwise outdated. For example, does anyone remember VisiCalc? VisiCalc gave way to Lotus 123, then Lotus 123 was overcome by Microsoft Excel. Over time, the CAPTCHA system became stale and had not been updated in three years. I’d recommend being suspicious of a any Plugin that hasn’t been updated recently, especially security related Plugins.
But even more, CAPTCHA technology itself has changed. Where CAPTCHA was once handled by asking the user for pattern matching or number readbacks, Google’s reCAPTCHA does a magical job at CAPTCHA, and does it more simply for the user.
Did you know that CAPTCHA stands for “completely automated public Turing test to tell computers and humans apart”
Fun facts!
Today I use “Google Captcha (reCAPTCHA) by BestWebSoft”. I have noticed that the development team doesn’t always stay on top of this Plugin. At one point, the Plugin hadn’t been updated in five months and was not tested on the more recent versions of WordPress. This is concerning, especially for a security related Plugin. At some point I might have to update this recommendation.
Login alerts
Elevated control users (such as Administrators and Editors) are able to modify system attributes. There is a potential for damaging changes to the site when these elevated control users login. Login alerts when elevated control users login helps to reduce the time under which they can do damage.
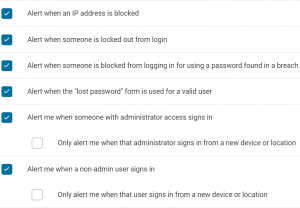
If the user is alerted when their identity logs in, they are quickly alerted if someone compromises their credentials. “Wordfence Security – Firewall & Malware Scan” By Wordfence (see link below) provides login alert capabilities.
Other options that should be enabled include Brute Force protection, Rate Limiting, forcing Strong Passwords, and Page View Rate Limiting, all of which is available in Wordfence.
Multi factor authentication
Multi factor authentication (often called “2 factor”) in large part fixes bad passwords. Compromising something you know (the password) is not sufficient to compromising the target system. The bad actor also needs to steal your badge or your finger (hopefully not the finger!)
NIST defines authentication factors as “something you know” (e.g., a password or a pin), “something you have” (e.g., a card, a badge, a key), and “something you are” (e.g, a biometric such as a fingerprint or iris scan).
See [Information Technology Laboratory, COMPUTER SECURITY RESOURCE CENTER, MFA]
Requiring every user to login with multiple factors makes it exceedingly more difficult for bad actors to gain a foothold.
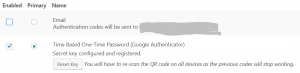
“Two-Factor By George Stephanis” is a great beginning at exploring multi factor options. There are many other options, but most are not free.
Let’s consider a few deeper discussions related to multi-factor and SMS. NIST recently deprecated or otherwise alerted as “inadvisable” SMS. The intent of SMS is that SMS is going to factor “something you have”. However, SMS is often “virtualized” with text messages going to multiple phones and even emails. If this happens, the authenticator is not guaranteed that the second factor is “something you have”. In fact, in the case of SMS going to email, it becomes only a multi-step login based on “two somethings you know” — a password to WordPress, and a password to the email account where SMS is going. This results in deprecating the “multi-factor” protection into a “multi-step” process. While “multi-step” may be sufficient in your particular environment, just be aware that multi-step is no longer multi-factor.
Automatic update
Automatic Updates sounds like the automatically correct thing to do, no? Well, the answer is an astounding maybe. Probably yes, but still maybe. Let’s look at a couple of thoughts here.
- Updating WordPress can wind up being a time consuming business. If this is you, that you don’t have the time to keep up your WordPress instance, I would recommend hiring someone to do it for you. That said, Automatic Updates might be a consideration.
- Not updating WordPress may result in wide open publicly known exploits. The vulnerability dwell time is the time during which the site is exposed to the vulnerability — that is, after the vulnerability is patched and before the patch is installed. During this time, the “world adversaries” know about the vulnerability and the world of WordPress is open to attack.
- Updating WordPress can result in incompatibilities bringing your site down. So… be careful! Even when you think you are doing the right thing, compromising your own system during the update is possible.
- The Update process itself may introduce vulnerabilities. Yes, you heard that right. WordPress relies on update links. An adversary can introduce code into bad links that will allow exploitation to your site. Read more here at Wordfence.
That all said, I highly recommend automatic updates wherever possible. I would recommend using Easy Updates Manager by the Easy Updates Manager Team if you are managing a single site.

Leave a Reply
You must be logged in to post a comment.